BleepingComputer.com
"AI-powered cursor IDE vulnerabilities to prompt injection attacks."
Views expressed in this cybersecurity, cyber crime update are those of the reporters and correspondents. Accessed on 01 August 2025, 1505 UTC.
Content and Source: "BleepingComputer.com."
URL-- https://www.bleepingcomputer.com/
Please check URL or scroll down to read your selections. Thanks for joining us today.
Russ Roberts (https://www.hawaiicybersecurityjournal.net).
Latest Articles-
AI-powered Cursor IDE vulnerable to prompt-injection attacks
Save $175 on a refurbished all-in-one Lenovo desktop deal
The Lenovo IdeaCentre 27″ AIO offers full desktop performance in a clean, all-in-one design that helps keep your space organized, and it's on sale. Instead of dropping $764.99 on one of these versatile desktops, you can get a refurbished one for $589.99.
- August 01, 2025
- 07:12 AM
 0
0
-
The Lenovo IdeaCentre 27″ AIO offers full desktop performance in a clean, all-in-one design that helps keep your space organized, and it's on sale. Instead of dropping $764.99 on one of these versatile desktops, you can get a refurbished one for $589.99.
- August 01, 2025
- 07:12 AM
 0
0
Identity attacks have changed — have your IR playbooks? 
Identity detection and response used to focus on on-prem Active Directory compromises. Today, identity attacks extend beyond the network, targeting cloud identities created, used, and exploited in the browser.
Join Push Security to learn about how identity attacks have evolved — and how IR playbooks need to adapt.
-
Identity detection and response used to focus on on-prem Active Directory compromises. Today, identity attacks extend beyond the network, targeting cloud identities created, used, and exploited in the browser.
Join Push Security to learn about how identity attacks have evolved — and how IR playbooks need to adapt.
Pwn2Own hacking contest pays $1 million for WhatsApp exploit
Kali Linux can now run in Apple containers on macOS systems
Microsoft to disable Excel workbook links to blocked file types
Microsoft now pays up to $40,000 for some .NET vulnerabilities
CISA open-sources Thorium platform for malware, forensic analysis
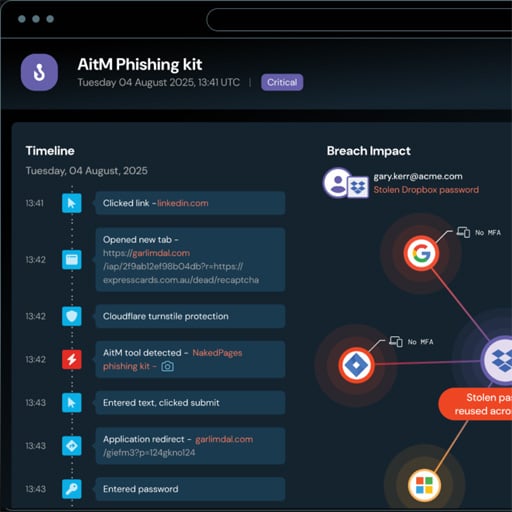
Microsoft: Russian hackers use ISP access to hack embassies in AiTM attacks
Inside a Real Clickfix Attack: How This Social Engineering Hack Unfolds
Spikes in malicious activity precede new security flaws in 80% of cases
Researchers have found that in roughly 80% of cases, spikes in malicious activity like network reconnaissance, targeted scanning, and brute-forcing attempts targeting edge networking devices are a precursor to the disclosure of new security vulnerabilities (CVEs) within six weeks.
- July 31, 2025
- 09:00 AM
 0
0
-
Researchers have found that in roughly 80% of cases, spikes in malicious activity like network reconnaissance, targeted scanning, and brute-forcing attempts targeting edge networking devices are a precursor to the disclosure of new security vulnerabilities (CVEs) within six weeks.
- July 31, 2025
- 09:00 AM
 0
0
Get this cybersecurity course and exam prep for life in this $53 deal
Whether you're looking to break into the cybersecurity industry or just want to better protect yourself online, this cybersecurity training and exam prep resource is worth checking out. Right now, you can get lifetime access for only $52.97 (reg. $280), and you don't need any coupons, either.
- July 31, 2025
- 07:10 AM
 0
0
-
Whether you're looking to break into the cybersecurity industry or just want to better protect yourself online, this cybersecurity training and exam prep resource is worth checking out. Right now, you can get lifetime access for only $52.97 (reg. $280), and you don't need any coupons, either.
- July 31, 2025
- 07:10 AM
 0
0
Proton launches free standalone cross-platform Authenticator app
ShinyHunters behind Salesforce data theft attacks at Qantas, Allianz Life, and LVMH
Hackers target Python devs in phishing attacks using fake PyPI site
SafePay ransomware threatens to leak 3.5TB of Ingram Micro data
Hackers actively exploit critical RCE in WordPress Alone theme
Hackers plant 4G Raspberry Pi on bank network in failed ATM heist
Apple patches security flaw exploited in Chrome zero-day attacks
New Lenovo UEFI firmware updates fix Secure Boot bypass flaws
AI Cuts vCISO Workload by 68% as Demand Skyrockets, New Report Finds
AI is reshaping vCISO services—and SMBs are fueling the surge. Cynomi's 2025 report shows 3x adoption growth and major workload drops as MSPs and MSSPs scale cybersecurity like never before. Learn more in the 2025 State of the vCISO Report.
- July 30, 2025
- 09:01 AM
 0
0
View More
AI is reshaping vCISO services—and SMBs are fueling the surge. Cynomi's 2025 report shows 3x adoption growth and major workload drops as MSPs and MSSPs scale cybersecurity like never before. Learn more in the 2025 State of the vCISO Report.
- July 30, 2025
- 09:01 AM
 0
0




















Comments
Post a Comment
Please leave a comment about our recent post.