Cyber War News Today.
- Get link
- X
- Other Apps
"From UPI to AI: Securing India's digital rise in an age of cyberwarfare."
Views expressed in this cybersecurity, cyberwarfare, and cyber crime update are those of the reporters and correspondents. Accessed on 31 July 2025, 1959 UTC.
Content and Source: "Cyber War News Today."
URL-- https://cyberwar.einnews.com/news/cyber-war-news?n=2&code=FA9GNesSTpp2rjO1&utm_source=NewsletterNews&utm_medium=email&utm_campaign=Cyber+War+News&utm_content=navig
Please check URL or scroll down to read your selections. Thanks for joining us today.
Russ Roberts (https://www.hawaiicybersecurityjournal.net).
Cyber War News Monitoring
- Published on 05:02 GMT

From UPI to AI: Securing India's digital rise in an age of cyberwarfare
In the vast landscape of India’s digital journey, where innovations like UPI, Aadhaar, ONDC, and AI-powered infrastructures have become the pillars of progress, the country is also witnessing a rising tide of sophisticated cyber threats. As the nation …
- Published on Jul 28, 2025

Cambodia escalates border attacks with heavy weapons, cyber warfare: Thai military
PUBLISHED : 28 Jul 2025 at 17:43 Cambodia has intensified its attacks along the Thai border, deploying additional troops, launching artillery strikes, and using cyber tactics, according to a report from Thailand’s Second Army Region. The military region, …
Source: Bangkok Post - Center-right - Published on 17:36 GMT

Dubai outstrips San Francisco for AI adoption and usage, report finds
Dubai ranks in the top five world cities in a new report on the adoption of artificial intelligence, beating San Francisco, widely considered the birthplace of the modern tech industry. Singapore took the top spot, according to Counterpoint Research, which …
Source: The National News - Pro-Government - Published on 17:49 GMT

Manus on MarketsInvestors digest a defiant Powell and bumper tech earnings
From tariff turmoil and stock shocks to market meltdowns, the global financial system has never been in such flux. Manus Cranny, The National's geo-economics editor, cuts through the noise and presents insights from the stories making headlines around …
Source: The National News - Pro-Government - Published on 11:06 GMT
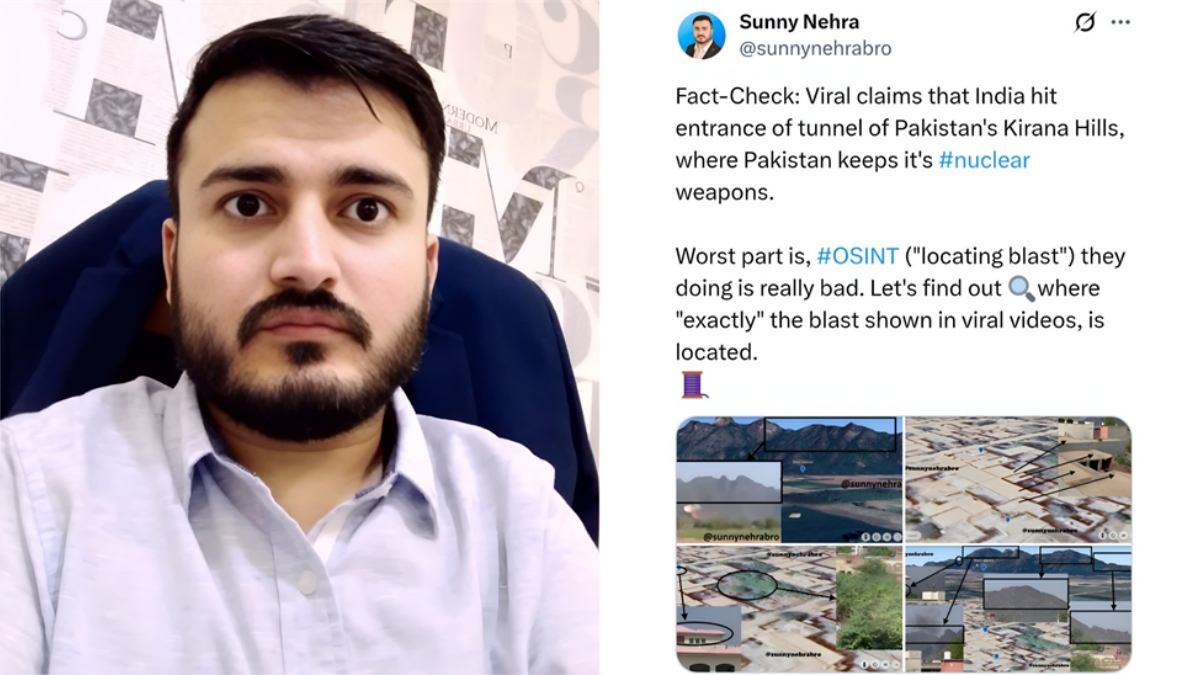
Top Hacker Sunny Nehra’s Viral Kirana Hills Thread Proven Very Accurate: New Satellite Images Confirm
In a resounding affirmation of the power of open-source intelligence (OSINT) or for the layman – “Cyber Intelligence”, recent high-resolution satellite images have confirmed the accuracy of a viral thread posted by Sunny Nehra, India’s top ethical hacker …
Source: News24 - Neutral - Published on 10:57 GMT
A deep dive into Australia’s cybersecurity legislative framework highlights critical regulatory and litigation ...
Key cybersecurity standards and requirements Australia’s cybersecurity legislative framework comprises federal, state and territory-based laws. The key legislative instruments are the Privacy Act 1988 (Cth) (the Privacy Act) and the Security of Critical …
Source: Global Investigations Review - Pending - Published on 11:32 GMT

APT Hackers Attacking Maritime and Shipping Industry to Launch Ransomware Attacks
The maritime industry, which facilitates approximately 90% of global trade, has emerged as a critical battleground for advanced persistent threat (APT) groups deploying sophisticated ransomware campaigns. This surge in cyber warfare represents a paradigm …
Source: Cyber Security News - Pending - Published on 04:12 GMT
East Jerusalem settlement plans 'devastating for peace'
On Jerusalem’s Mount Scopus, the sites most familiar in the decades-long fight for land – Al Aqsa Mosque flanked by the Western Wall, the Church of the Holy Sepulchre, the neighbourhood of Sheikh Jarrah – can be seen. Turn, and below the desert hills of …
Source: The National News - Pro-Government - Published on Jul 30, 2025

NATO’s Arming For World War III Aimed At Preventing Clash With Russia
Leading-edge French Rafale combat aircraft takes off - NATO chief Mark Rutte says Europe needs more jet fighters, more modern tanks, and more missiles to match Russia's arms build-up. (Photo by Fred TANNEAU / AFP) (Photo by FRED TANNEAU/AFP via …
Source: Forbes - Neutral - Published on Jul 30, 2025

Why Microsoft Must Be Held Responsible For Its Pentagon Security Breach
Imagine leaving your front door unlocked with a note that reads, “Back in 15. Please don’t steal the silverware.” That, in essence, is what the United States government — yes, including the Pentagon — may have unwittingly done through its long-standing …
Source: Daily Wire - Right-wing - Published on Jul 30, 2025

Op Sindoor a wake-up call for smart ammo, AI-ready warfare: Lt Gen Aujla
The Indian Army's Lt Gen Amardeep Singh Aujla outlined a comprehensive vision for modern warfare and ammunition strategy, especially in the aftermath of Operation Sindoor. Speaking at the Ammo Power Conference, he stated, “We have just undertaken Phase …
Source: India Today - Neutral - Published on Jul 30, 2025

3 threats for Ireland's new maritime security strategy to solve
Analysis: The strategy comes at a time when Ireland stands at a critical juncture in defining how it will protect one of Europe's largest sea areas By the end of 2025, Ireland will have its first ever National Maritime Security Strategy, intended to …
Source: RTE Ireland - Public Broadcaster - Published on Jul 30, 2025

The EU has a bone to pick with Temu
Good morning. Fortune released its new Global 500 yesterday. For the unfamiliar, it’s our annual ranking of the world’s largest companies by revenue—not to be confused with the famous Fortune 500, which is limited to the U.S. Who’s up and who’s down in …
Source: Fortune - Neutral - Published on Jul 30, 2025

New UA Little Rock Course Prepares Students to Secure Critical Infrastructure
Angelita Faller | July 30, 2025 UA Little Rock's cybersecurity faculty include Philip Huff bottom left, Bill Cox, top left, Sandra Leiterman, center left, Rebecca Passmore, center right, and Phuong Tran, right. Photo by Benjamin Krain. UA Little Rock …
Source: UA Little Rock - Arkansas - Pending - Published on Jul 30, 2025

What the Israel-Iran conflict revealed about wartime cyber operations
New Atlanticist July 30, 2025 • 9:16 am ET Print this page By Nikita Shah The recent war between Iran and Israel will be remembered for what the world witnessed—from the direct, large-scale military strikes by both countries (and the United States), to a …
Source: Atlantic Council - Indeterminate - Published on Jul 30, 2025

Lazarus Group hackers increase open-source weaponisation
North Korea’s infamous Lazarus Group hackers are increasing their weaponisation of open-source software, according to a new Sonatype report. The state-sponsored hackers are hiding malicious code inside seemingly normal software packages to steal secrets …
Source: Developer Tech News - Pending - Published on Jul 30, 2025

Indonesia’s grand strategy for integrated deterrence and defense modernization
hile most people may not be aware, the Perisai Trisula Nusantara, or Nusantara Trident Shield (NTS) defense vision, represents a bold and ambitious evolution of Indonesia’s earlier Minimum Essential Force (MEF) program. Introduced by President Prabowo …
Source: The Jakarta Post - Neutral - Published on Jul 30, 2025

Baltic security: Keeping an eye on the Kremlin
Russia looks to be preparing major NATO provocations, including hybrid attacks and military buildup near Nordic borders, and may test Article 5. Lithuanian soldiers stand with drones during the NATO Quadriga military exercise, in Pabrade, Lithuania, on May …
Source: Geopolitical Intelligence Services - Neutral - Published on Jul 18, 2025
The Cat-and-Mouse Cyber War—and How to Win It
Why Proper API Implementations Fail Many APIs are custom-built, and their development quality is often lacking. During creation, numerous errors can arise, and the interaction model may not be thoroughly tested. As a result, unexpected data can sometimes …
Source: SecurityInfoWatch.com - Pending
- Get link
- X
- Other Apps


Comments
Post a Comment
Please leave a comment about our recent post.